Patch Management Automation
An automated patch management solution increases complex software development efficiency concurrently ensuring a high level of vulnerability remediation in a reasonable time frame.
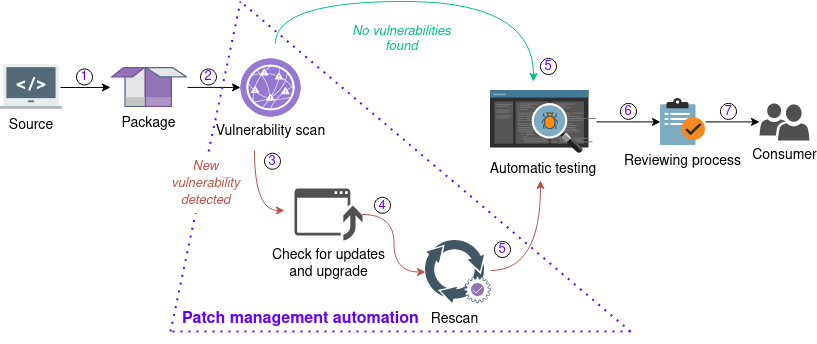
The patch management automation (PMA) system processes data in cycles. Every cycle includes a number of stages:
- The developer submits the change to the repository. Hydra builds the package from the source.
- The Vulnerability Analysis (VA) component scans each software artifact for vulnerabilities immediately after the build.
- If new vulnerabilities are discovered, the PMA system scans each dependency provenance for the update availability.
- If update availability exists, the PMA system downloads new dependencies, and Hydra builds the new package.
- The package is rebuilding with updated dependencies that may affect functionality. The PMA system starts the package regression testing.
- A package passing the testing will be presented to the concerned developers for review and approval. The SBOM, scan and test results along with the package are published to a web server. The developer downloads the artifacts for review and approval.
- All approved artifacts become release candidates and can be found on the web server.
Implementation
Section titled “Implementation”Dependency Tracking
Section titled “Dependency Tracking”The dependency tracking solution is based on Package URL (PURL), natively supported by ClyconeDX. PURL is a URL, composed of seven components:
scheme:type/namespace/name@version?qualifiers#subpath
- scheme: URL scheme, with the constant value “pkg”, facilitating the future official registration of the “pkg” scheme for package URLs.
- type: the package type, such as npm, maven, etc.
- namespace: name prefix. For example GitHub user, organization, etc.
- name: the name of the package.
- version: the version of the package.
- qualifiers: extra qualifying data, e.g. OS, distro, architecture, etc.
- subpath: extra subpath relative to package root.
In addition to PURL, each component should contain at least one hash value, computed from cryptographic hash functions. The hash values help to verify the original package integrity and source prior to update the download. Thus minimizing security risks during the process.
Package Update
Section titled “Package Update”The update mechanism implementation depends on a system and will differ from one build system to another.
For example, in Nix it is enough that respective Nix files are automatically updated and the package is rebuilt. For more information on package update steps, see the Update a package article of the NixOS Wiki.